Development
Introduction
At Jovasi Technology, we have extensive experience in creating bespoke software and backend systems for organisations of all sizes. Whether it's a desktop application, mobile app, complex web application or your company's customer facing website, we can produce an easy-to-use design which allows your users to achieve their end goals whilst interacting with your products and services.Windows Applications
From simple Windows based applications to complex client/server solutions.Mobile Apps
Designing company mobiles apps for Android & IOS devices.Web Applications
From simple websites to complex web applications, for any type of solution.Internet of Things
Our hardware design experts can help develop your IoT based devices.Data Compliance
Ensure your applications are compliant with regulations such as GDPR and COPPA.Database Design
We can design your data storage needs such as SQL, NoSQL, REDIS, Big Data.
How We Work
In working with us, you will receive impartial and competent advice and support, with the highest levels of technical expertise. Our approach to software development is one of discovery and collaboration, and our consultants strive to understand your requirements, strategies and goals.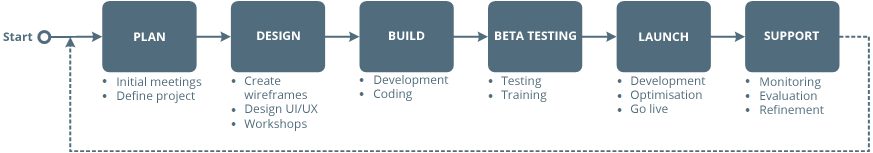
Meeting & Strategy
Whatever your chosen platform, it ultimately needs to support your goals. We take a strategic approach to the software development, and work with you to define your requirements. By researching your industry, market and competitors, we will use our technical expertise to gather the information required to advice you on the best solution and platform.
During the initial meetings, we will discuss your requirements in detail to ensure we work towards your goals, and outline a realistic solution, timeline and cost structure.
Design & User Experience
Within the design phase, we explore your concept, start working on the user experience workflow by illustrating each screen, action and process. This helps us highlight potential issues early on, and put measures in place to prevent them.
Once we are both satisfied with the concept, we can move on to a wireframe design of your solution, at which point you start to get an idea of the end product. Once this stage is approved, our designers will produce a few screenshots using your preferred design for feedback.
Build
The build stage is where the software actually gets coded. Using the workflows, wireframes and designs - our developers use their expertise to create professional products which are optimised for your platform and end users. During the build stage, we continually debug and test your software for potential issues.Testing
Your product will be tested under different conditions, operating systems and platforms to simulate a variety environments that it is likely to face. Once we are satisfied, we will present you with the software for review and further testing.
After the testing and bug-fixing period, we will do a final wrap and officially handover the product. We will provide guidance on installing the software on your preferred system, and will continue to support you with resolving issues until the product is ready to go live.
Going Live
On the launch date, our project management team and technical experts will work with you to ensure things go as smooth as possible.Security & Compliance
At Jovasi Technology, we strongly believe in designing software and systems that are secure and compliant with current regulations. We believe it is not enough to test the software only at the required stages, as this can result in overlooking minor vulnerabilities.Secure Development Lifecycle
The Secure Development Lifecycle (SDL) is the process of including security artefacts in the Software Development Lifecycle (SDLC). The main benefits of adopting a secure SDLC is that it makes security a continuous concern for those involved, and exposes issues early in the development process, thus reducing time and costs later on in the development process. Risk Assessment – discover and identify any potential risks associated with the application or environment.
Risk Assessment – discover and identify any potential risks associated with the application or environment. Discovery - determine the security objectives required by the software, what are the possible threats and what regulations the organisation needs to follow.
Discovery - determine the security objectives required by the software, what are the possible threats and what regulations the organisation needs to follow. Threat Modelling – models the software components to identify and manage threats early in the development lifecycle.
Threat Modelling – models the software components to identify and manage threats early in the development lifecycle. Design Review - ensure the software is built with the most secure features. When reviewing the code, developers need to be aware of the most common coding security pitfalls.
Design Review - ensure the software is built with the most secure features. When reviewing the code, developers need to be aware of the most common coding security pitfalls. Static Analysis - identifies the exact location of weaknesses by analyzing the software without executing it.
Static Analysis - identifies the exact location of weaknesses by analyzing the software without executing it. Security Testing - checks how vulnerable is the new product to attacks.
Security Testing - checks how vulnerable is the new product to attacks. Code Review – checks a program mainly by viewing and reading parts of its source code.
Code Review – checks a program mainly by viewing and reading parts of its source code. Secure Configuration – refers to security measures that are implemented when developing systems in order to reduce unnecessary vulnerabilities.
Secure Configuration – refers to security measures that are implemented when developing systems in order to reduce unnecessary vulnerabilities.Data Compliance
With the introduction of GDPR and the Data Protection Act 2018, software developers need to ensure more than ever that their applications are in compliance with the data protection regulations right from the design stage.If the software is targeted towards children, then there is the added requirements of complying with additional data protection laws (such as COPPA and GDPR-K). Applications may need explicit consent from the user, and can only be collected under specific circumstances.
 IT Consultancy
IT Consultancy Project Management
Project Management Data Protection
Data Protection Network Design
Network Design WAN & VPN
WAN & VPN Wi-Fi & Guest Portals
Wi-Fi & Guest Portals Cloud (AWS/Azure)
Cloud (AWS/Azure) Server Infrastructure
Server Infrastructure Active Directory
Active Directory Storage
Storage Backup & DR
Backup & DR 5-Step Cyber Health Check
5-Step Cyber Health Check NCSC Cyber Advisor
NCSC Cyber Advisor Virtual CISO
Virtual CISO Virtual DPO
Virtual DPO Accreditation
Accreditation Secure Architecture
Secure Architecture Vulnerability Scans
Vulnerability Scans Secure Destruction
Secure Destruction Incident Response
Incident Response Windows Applications
Windows Applications Mobile Apps
Mobile Apps Web Applications
Web Applications Internet of Things
Internet of Things Artificial Intelligence
Artificial Intelligence Data Compliance
Data Compliance Database Design
Database Design Support Home
Support Home News & Blogs
News & Blogs FAQs
FAQs Contact Us
Contact Us Company
Company
























 Call
Call Contact Us
Contact Us